OWASP web goat source code SQL injection code vulnerability
For this post, I have to give credit to OWASP for creating web goat. I scanned the vulnerable application with different commercial static code analysis analyzers which allow the user to see the code behind the vulnerabilities.
public String getRawParameter(String name) throws ParameterNotFoundException
{
String[] values = request.getParameterValues(name);
if (values == null)
{
throw new ParameterNotFoundException(name + " not found");
}
else if (values[0].length() == 0) { throw new ParameterNotFoundException(name + " was empty"); }
return (values[0]);
Notice that there is not a validation mechanism for the values USERNAME and PASSWORD.
try
{
String username = "";
String password = "";
username = s.getParser().getRawParameter(USERNAME);
password = s.getParser().getRawParameter(PASSWORD);
// If they get back more than one user they succeeded
if (results.getRow() >= 1)
{
// Make sure this isn't data from an sql injected query.
if (results.getString(2).equals(username) && results.getString(3).equals(password))
{
String insertData1 = "INSERT INTO user_login VALUES ( '" + username + "', '"
+ s.getUserName() + "' )";
statement.executeUpdate(insertData1);
}
// check the total count of logins
query = "SELECT * FROM user_login WHERE webgoat_user = '" + s.getUserName() + "'";
results = statement.executeQuery(query);
results.last();
// If they get back more than one user they succeeded
if (results.getRow() >= 3)
{
makeSuccess(s);
Above is the visual smart trace of the SQL injection code so you can visually see it and understand it. The red boxes are sources and sinks. The blue boxes are sinks as well. The grey boxes allow code to pass through them. The grey boxes should have validation mechanisms in them. Those grey boxes don’t and this allows for SQL injection. Webgoat by design, is also using dynamic SQL statements and not parameterized queries which allow for SQL injection that it teaches on the front end of the lessson.
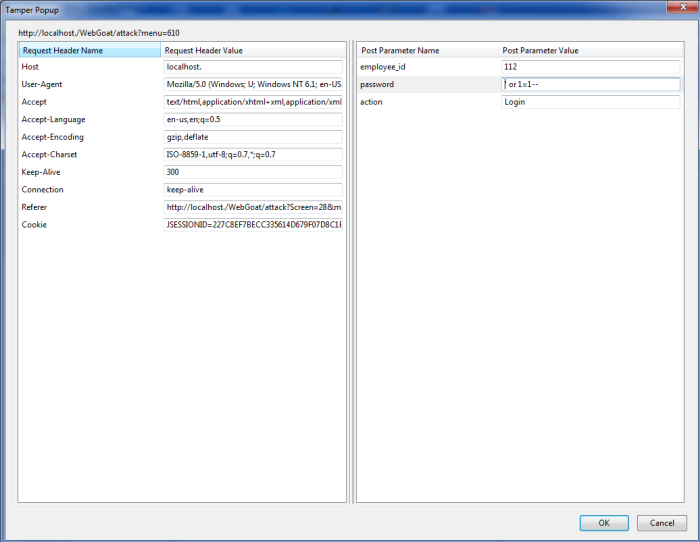
Here are the screen shots of the application which is vulnerable to SQL injection. Thanks for Aspect Security for creating this application.
My passion is software security and linking web penetration testing with source code analysis.
Matt Parsons, CISSP, MSM, mparsons1980@gmail.com



[…] This post was mentioned on Twitter by Dinis Cruz, Matt Parsons. Matt Parsons said: OWASP web goat source code SQL injection code vulnerability http://wp.me/p1aH0u-2Z […]
Tweets that mention OWASP web goat source code SQL injection code vulnerability « parsonsisconsulting -- Topsy.com
February 5, 2011 at 12:57 am
Hello! It seems as though we both have a interest for the same thing.
Your blog, “OWASP web goat source code SQL injection code vulnerability | parsonsisconsulting” and mine are very similar.
Have you ever thought about writing a guest article for a related blog?
It will definitely help gain publicity to your blog (my site recieves a
lot of traffic). If you happen to be interested, email me at: cornellmanuel@gmail.
com. Thank you so much
online work from internet
February 27, 2013 at 7:18 am
What’s up it’s me, I am also visiting this site regularly, this web site is genuinely good and the users are truly sharing nice thoughts.
patrick
March 20, 2013 at 1:01 am